Network Access Control (NAC)
A Comprehensive Technical Analysis
Network Access Control (NAC) represents a cornerstone of modern cybersecurity strategy, providing organizations with critical capabilities to manage and secure network access in increasingly complex and diverse IT environments. Driven by trends such as Bring Your Own Device (BYOD), the proliferation of Internet of Things (IoT) devices, distributed workforces, and evolving cyber threats, traditional perimeter-based security is no longer sufficient. NAC addresses this gap by implementing policy-based control over network access, regardless of how or where users and devices connect.
This report provides an in-depth technical analysis of NAC, exploring its fundamental concepts, core operational mechanisms including authentication, authorization, and endpoint posture assessment and various enforcement models. It examines how NAC integrates with the broader security ecosystem, enhancing visibility and enabling automated responses. A comparative analysis of leading NAC solutions offers insights into the vendor landscape. Furthermore, the report delves into the practical challenges and best practices associated with NAC implementation and management, illustrates its application across different industries, and clarifies its role in achieving regulatory compliance. Finally, it explores advanced concepts and emerging trends, such as NAC's pivotal role in Zero Trust Architecture, the rise of cloud-based NAC offerings, and enhanced strategies for securing IoT devices. The analysis concludes that NAC is not merely a technology but a strategic imperative for organizations seeking to establish robust, adaptive, and compliant network security postures.
1. Introduction to Network Access Control (NAC)
1.1. Defining NAC
Network Access Control (NAC) is a comprehensive network security solution designed to enforce policies, control access, and enhance the security posture of an organization's network infrastructure. At its core, NAC acts as a sophisticated gatekeeper, determining who (users) and what (devices) can connect to the network, and subsequently, what resources they are permitted to access once connected. It functions by identifying users and devices, verifying their compliance with security policies, authenticating their credentials, authorizing appropriate access levels, and continuously monitoring activity post-connection. A primary function of NAC is to prevent unauthorized users or non-compliant devices from gaining access, thereby mitigating risks associated with compromised endpoints or malicious actors. It ensures that even authorized entities adhere to predefined security rules throughout their network session.
1.2. The Imperative for NAC in Modern Networks
The contemporary network landscape is characterized by dissolving perimeters and increasing complexity, making robust access control mechanisms more critical than ever. Several key trends underscore the necessity for NAC:
Device Proliferation: The explosion of Bring Your Own Device (BYOD) policies and the integration of countless Internet of Things (IoT) devices introduce a vast array of endpoints with varying security postures onto the network.
Mobility and Remote Access: Users connect from diverse locations using multiple device types, challenging traditional network boundaries and requiring consistent policy enforcement regardless of connection point.
Sophisticated Threats: Attackers increasingly target endpoints as entry vectors, necessitating checks on device health and user identity before granting access.
Regulatory Compliance: Mandates such as HIPAA, PCI DSS, and GDPR require stringent controls over data access and network segmentation, which NAC helps enforce.
These factors render traditional perimeter security insufficient. NAC provides essential visibility and granular control over this dynamic environment, allowing administrators to manage access based on context (user identity, device type, location, compliance status) rather than just network location.
1.3. Core Functions and Goals
NAC solutions aim to achieve several strategic security objectives:
Enhance Security Posture: By preventing unauthorized access and ensuring connecting devices meet security standards, NAC significantly reduces the network's attack surface.
Enforce Compliance: NAC helps organizations meet regulatory and internal policy requirements through automated policy enforcement and detailed audit trails.
Improve Visibility: NAC provides insights into who and what is connected to the network, offering crucial context for security operations.
Automate Access Control: NAC automates the process of authentication, authorization, and remediation, reducing administrative overhead and ensuring consistent policy application.
Enable Secure Mobility, BYOD, and IoT: NAC provides the framework to securely integrate diverse device types and support mobile work styles.
To achieve these goals, NAC performs several core functions:
Identification and Profiling: Discovering and classifying devices attempting network access.
Authentication: Verifying the identity of users and/or devices.
Authorization: Determining the appropriate level of network access based on policy.
Posture Assessment: Evaluating the security health and compliance of endpoints.
Policy Enforcement: Applying access rules (e.g., VLAN assignment, ACLs).
Monitoring: Observing device activity post-admission.
Remediation: Guiding non-compliant devices towards compliance or isolating them.
While NAC offers extensive capabilities for managing network access, it functions most effectively as part of a layered security architecture. Its primary strength lies in controlling access based on identity and posture. However, it may have limitations in detecting sophisticated post-admission threats or handling certain types of unmanaged devices without assistance. Therefore, integrating NAC with other security technologies, such as firewalls, IDPS, SIEM, and EDR (as discussed in Section 4), is crucial for comprehensive protection. NAC serves as a foundational control layer, setting the stage for secure network operations but requiring collaboration with other tools to address the full spectrum of modern cyber threats.
2. Core NAC Mechanisms In-Depth
NAC systems employ several core mechanisms to identify, authenticate, authorize, and assess connecting entities. Understanding these mechanisms is crucial for designing and implementing effective NAC policies.
2.1. Authentication: Verifying Identity
Authentication confirms the identity of the user or device attempting to connect. NAC supports multiple methods, often used in combination depending on the device type and security requirements.
2.1.1. IEEE 802.1X: The Standard for Port-Based Authentication
The IEEE 802.1X standard provides a robust framework for port-based network access control (PNAC), enabling centralized authentication for devices connecting to LANs or WLANs. It is widely considered the most secure common authentication method for NAC.
The 802.1X framework involves three key components:
Supplicant: Software running on the endpoint device (e.g., laptop, smartphone) that responds to authentication requests from the network. Many modern operating systems have built-in supplicants.
Authenticator: The network access device (NAD), such as an Ethernet switch or wireless access point (AP), that acts as an intermediary. It blocks traffic until authentication succeeds and relays authentication messages between the supplicant and the authentication server.
Authentication Server (AS): Typically a RADIUS (Remote Authentication Dial-In User Service) server, which validates the supplicant's credentials against an identity store (e.g., Active Directory, LDAP, internal database) and sends an authorization decision back to the authenticator.
The communication process relies on the Extensible Authentication Protocol (EAP), which provides a framework for various authentication methods. EAP messages between the supplicant and authenticator are encapsulated in EAP over LAN (EAPoL) frames for wired and wireless networks. The authenticator then translates these EAP messages into RADIUS packets for communication with the authentication server.
A typical 802.1X authentication flow proceeds as follows:
Initiation: The supplicant connects to a port on the authenticator, or the authenticator detects a new connection. The authenticator initially blocks all traffic except EAPoL.
Identity Request: The authenticator sends an EAP-Request/Identity message to the supplicant.
Identity Response: The supplicant responds with an EAP-Response/Identity message containing its user or device identity.
Relay to AS: The authenticator encapsulates the EAP response in a RADIUS Access-Request packet and forwards it to the authentication server.
Challenge/Response: The authentication server initiates an EAP method-specific challenge-response sequence (negotiated between supplicant and AS, relayed by the authenticator) to verify the supplicant's credentials or certificate.
Authentication Decision: Based on the outcome, the AS sends a RADIUS Access-Accept or Access-Reject message back to the authenticator.
Port Control: If Access-Accept is received, the authenticator opens the port, allowing normal traffic flow for the supplicant. If Access-Reject is received, the port remains blocked.
Common EAP methods used within the 802.1X framework include:
EAP-TLS (Transport Layer Security): Highly secure, requires both client-side and server-side certificates for mutual authentication.
EAP-TTLS (Tunneled TLS): Uses a server-side certificate to create a secure tunnel, within which client authentication occurs using simpler methods (e.g., username/password - PAP, CHAP, MS-CHAPv2).
PEAP (Protected EAP): Similar to EAP-TTLS, uses a server-side certificate for tunneling. Commonly uses MS-CHAPv2 for inner authentication. EAP-PEAP is widely used.
Configuring 802.1X involves enabling AAA (Authentication, Authorization, Accounting) services, defining RADIUS server details (IP address, shared secret, ports), and enabling 802.1X on specific switch ports or WLANs. Compared to simpler methods like WPA2 Pre-Shared Keys (PSK) for Wi-Fi, 802.1X offers significantly enhanced security by requiring unique credentials or certificates per user/device, preventing unauthorized access even if a single password is compromised.
2.1.2. MAC Authentication Bypass (MAB): Handling Non-Supplicant Devices
While 802.1X provides strong security, many devices lack the necessary supplicant software to participate in EAP authentication. These often include printers, IP cameras, IoT sensors, VoIP phones, and older legacy systems. For these scenarios, MAC Authentication Bypass (MAB) serves as an alternative or fallback mechanism.
MAB utilizes the device's unique hardware identifier, the Media Access Control (MAC) address, for authentication. The workflow is as follows:
A device connects to a MAB-enabled port. The switch attempts 802.1X first (if configured as primary).
If the device does not respond with EAPoL messages (indicating no 802.1X supplicant), the switch captures the source MAC address from the first frame(s) it receives (excluding control plane traffic like CDP, LLDP).
The switch sends a RADIUS Access-Request to the authentication server, typically using the MAC address as both the username and password.
The RADIUS server checks its database to see if the MAC address is registered and permitted access.
The RADIUS server responds with Access-Accept or Access-Reject. If accepted, the switch opens the port.
MAB is often configured as a fallback mechanism; the network attempts 802.1X first, and only if that fails or times out does it try MAB. Different MAB modes exist to control how many devices can be authenticated on a single port:
Single-host mode: Only the first MAC address detected is authenticated; subsequent MACs trigger a security violation (default on some platforms).
Multi-domain authentication host mode: Allows two MAC addresses, typically one for an IP phone (in the voice VLAN) and one for a PC connected through the phone (in the data VLAN).
Multi-authentication host mode: Authenticates multiple devices individually on the same port (e.g., connecting to another switch).
Multi-host mode: Authenticates only the first MAC address; all subsequent devices on the port are permitted without further authentication. This mode is less secure but simpler in certain scenarios.
Despite its utility for non-802.1X devices, MAB is inherently insecure. MAC addresses are transmitted in the clear and can be easily captured and spoofed (imitated) by attackers. An attacker can simply change their device's MAC address to match an authorized device (like a printer) and gain network access. For this reason, MAB should be considered a "bypass" of strong authentication, used only when necessary and coupled with compensating controls.
Mitigation strategies include:
Strict Network Segmentation: Placing MAB-authenticated devices into highly restricted VLANs with granular ACLs that limit their communication to only essential services.
Device Profiling: Combining MAB with NAC profiling capabilities. The NAC system checks if the device characteristics (e.g., DHCP fingerprint, open ports, OS type) match the expected profile for the registered MAC address. Discrepancies can indicate spoofing. Techniques like DHCP gleaning can assist profiling.
Limited Use: Employing MAB only for devices genuinely incapable of 802.1X and phasing out such devices where possible.
2.1.3. Captive Portals: Web-Based Authentication and Onboarding
Captive portals provide a web-based interface for user authentication, policy acceptance, or device registration, commonly used for guest access and BYOD onboarding. When an unauthenticated user attempts to access the network (usually via Wi-Fi, but also possible on wired networks), their web traffic is intercepted and redirected to a specific login page hosted by the NAC system, a wireless controller, or a dedicated portal server.
The typical captive portal workflow involves several steps:
Connection & Redirection: The user connects to the network (e.g., a guest SSID). Initial access is restricted (often only DNS and DHCP). When the user opens a web browser, their HTTP/HTTPS request is intercepted, and they are redirected to the portal URL.
Portal Interaction: The user is presented with the captive portal page, which may require:
Login with predefined credentials (e.g., guest accounts, employee directory accounts).
Self-registration (providing details like name, email, phone number).
Use of vouchers or access codes.
Social media login integration.
Acceptance of an Acceptable Use Policy (AUP).
Device onboarding steps (e.g., downloading a configuration profile).
Authentication: Credentials or registration information submitted via the portal are typically validated against a backend authentication server (e.g., RADIUS, LDAP, Cloud Identity Provider like Azure AD via SAML).
Authorization Update: Upon successful authentication/acceptance, the NAC system authorizes broader network access. This might involve sending a RADIUS Change of Authorization (CoA) message to the network device (switch/controller) to update the user's session attributes (e.g., assign a different VLAN or ACL).
Technical considerations for captive portals include:
DNS and HTTP/HTTPS Handling: The system must reliably intercept traffic for redirection. Handling HTTPS requires careful certificate management to avoid browser trust warnings; using publicly signed certificates is highly recommended.
Controller vs. Server Initiated: In controller-initiated flows, the network device handles the credential submission; in server-initiated flows (like ClearPass or ISE web auth), the portal interacts more directly with the NAC server.
MAC Caching: To improve user experience, NAC systems often cache the MAC addresses of successfully authenticated portal users for a period. Subsequent connections from the same device bypass the portal via MAC authentication. However, this can introduce complexities, especially during roaming between access points.
Integration: Portals can integrate with various identity sources and can be used as part of BYOD onboarding workflows to provision devices with certificates or network profiles.
The choice and combination of authentication methods—802.1X, MAB, and Captive Portals—involve inherent trade-offs. 802.1X offers the highest level of security through strong cryptographic protocols and unique credentials/certificates but demands compatible supplicants on endpoints and can involve deployment complexity. MAB provides broad compatibility, enabling network access for devices incapable of 802.1X, but at the cost of significantly lower security due to the ease of MAC spoofing. Captive Portals offer a user-friendly (browser-based) approach for guest access and BYOD onboarding, maximizing usability for transient users, but they introduce potential user friction through redirection and login steps, and require careful handling of web protocols and certificates. Consequently, organizations rarely rely on a single method. Instead, they typically implement a multi-tiered authentication policy that prioritizes the most secure method available for a given device (e.g., attempting 802.1X first), falling back to less secure methods like MAB only when necessary and implementing compensating controls, while reserving captive portals for specific use cases like guest access where usability is paramount. This layered strategy allows organizations to balance security requirements, device compatibility, and user experience across their diverse network environment.
2.2. Authorization: Defining Access Privileges
Once a user or device is authenticated, authorization determines what network resources they can access. NAC enforces authorization dynamically based on policies linked to the authenticated identity, role, device type, or posture status.
2.2.1. Dynamic VLAN Assignment: Network Segmentation
A fundamental authorization technique is dynamically assigning authenticated entities to specific Virtual Local Area Networks (VLANs). VLANs logically segment a physical network into separate broadcast domains, isolating traffic between different groups of users or devices.
NAC leverages the RADIUS protocol to achieve dynamic VLAN assignment. During the authentication process, if the user/device is successfully authenticated, the RADIUS server includes specific attributes in the Access-Accept message sent back to the authenticator (switch or AP). Common attributes used for VLAN assignment include:
Tunnel-Private-Group-ID (RADIUS Standard IETF Attribute 81)
Egress-VLAN-ID or Egress-VLAN-Name (Vendor-specific or IETF, often specifying tagged/untagged status)
Upon receiving these attributes, the network device dynamically configures the port or wireless session to belong to the specified VLAN for the duration of the session. This allows administrators to enforce segmentation based on policy rather than static port configurations.
Benefits of dynamic VLAN assignment include:
Policy-Based Segmentation: Grouping users/devices by role (e.g., Sales, Engineering, Guest), device type (e.g., PCs, IP Phones, IoT), or trust level (e.g., Compliant, Non-Compliant/Quarantine).
Enhanced Security: Isolating sensitive systems and limiting the lateral movement of threats. Traffic between VLANs typically must pass through a Layer 3 device (router or firewall), where further filtering can be applied.
Operational Efficiency: Simplifies network administration. Instead of manually configuring VLANs on potentially thousands of switch ports, policies are managed centrally on the NAC/RADIUS server. This supports concepts like "colorless ports," where all access ports have a generic initial configuration, and the specific VLAN and policy are applied dynamically after authentication.
Flexibility: Enables use cases like Personal Area Networks (PANs) in hospitality, where each guest room can be assigned a private VLAN dynamically, allowing a guest's devices to communicate while being isolated from other guests.
Challenges include ensuring the assigned VLANs are configured on upstream network devices and handling specific scenarios like IP phones that often require both a data VLAN (for a connected PC) and a voice VLAN. While some platforms support dynamic assignment of voice VLANs via RADIUS, often Link Layer Discovery Protocol (LLDP) or static port configuration is still used for voice VLAN assignment. Additionally, careful consideration must be given to behavior during RADIUS server outages; mechanisms like critical VLAN assignment or cached role information can provide fallback access. Dynamic VLAN assignment can also improve performance in some architectures by moving authenticated users off bottleneck devices like captive portal gateways onto dedicated VLANs handled at wire speed.
2.2.2. Access Control Lists (ACLs): Granular Traffic Filtering
While VLANs provide network segmentation at Layer 2, Access Control Lists (ACLs) offer more granular control at Layer 3 (IP) and Layer 4 (TCP/UDP ports). NAC systems can dynamically assign ACLs to authenticated sessions, further refining access permissions.
Similar to dynamic VLANs, dynamic ACLs (dACLs) or filter rules are typically delivered via RADIUS attributes in the Access-Accept message. Common attributes include:
Filter-Id (RADIUS Standard IETF Attribute 11): Specifies the name of a pre-defined ACL on the network device.
Vendor-Specific Attributes (VSAs): Allow sending the actual ACL rules directly within the RADIUS packet (e.g., Cisco's cisco-av-pair=ip:inacl#<n>=<rule>).
These dynamically applied ACLs filter traffic for the specific user or device session, allowing or denying communication based on source/destination IP addresses, protocols, and ports.
Use cases for dynamic ACLs include:
Implementing Least Privilege: Restricting users or devices to access only the specific servers, applications, or network segments required for their function, even within the same VLAN.
Quarantine/Remediation: Applying highly restrictive ACLs to non-compliant devices, permitting access only to remediation servers (e.g., patch servers, antivirus update sites) while blocking access to internal resources or the internet.
IoT Device Containment: Limiting IoT devices (often authenticated via MAB) to communicate only with their designated management platforms or controllers.
Context-Aware Access: Applying different ACLs based on user role, device type, location, or compliance status.
Dynamic ACLs offer significant advantages over static ACLs configured directly on network devices. They are context-aware, applied per-session based on real-time authentication and policy evaluation. This provides greater flexibility and scalability, especially in large environments, as ACL management is centralized within the NAC policy engine rather than distributed across numerous network devices.
2.2.3. Role-Based Access Control (RBAC) Integration: Policy Based on Function
Role-Based Access Control (RBAC) is a security paradigm where access permissions are assigned based on roles within an organization, rather than directly to individual users. Roles (e.g., "Sales Representative," "Network Administrator," "Doctor," "Guest") are defined based on job functions and responsibilities, and each role is granted a specific set of permissions. Users are then assigned to one or more roles.
NAC systems effectively leverage RBAC principles for authorization. The process typically works as follows:
A user authenticates to the network (e.g., via 802.1X).
The NAC system queries an identity source (like Active Directory, LDAP, or a cloud identity provider) to determine the user's group memberships, which correspond to predefined roles.
The NAC policy engine evaluates policies associated with the user's determined role(s).
Based on the role, the NAC system instructs the network device (via RADIUS attributes) to apply the appropriate authorization controls, such as assigning the user to a specific VLAN and/or applying a specific dynamic ACL.
It's important to distinguish between NAC's role in network access and RBAC's broader application to resource and application access. NAC primarily controls entry to the network and enforces network-level segmentation (VLANs, ACLs) based on role. Deeper RBAC controls within applications or operating systems determine what actions a user can perform after accessing a resource. They are complementary: NAC uses role information to enforce network boundaries, while application-level RBAC enforces permissions within those boundaries.
Integrating RBAC with NAC offers significant benefits:
Simplified Administration: Administrators manage permissions at the role level. When a user changes jobs, only their role assignment needs updating, automatically adjusting their network access rights.
Consistency: Ensures uniform application of access policies for all users within the same role.
Alignment with Business Structure: Access policies directly reflect organizational structure and responsibilities.
Improved Compliance: Facilitates demonstrating that access is granted based on need-to-know principles defined by roles.
Effective RBAC within NAC requires careful planning, including defining clear roles, mapping roles to appropriate network access policies (VLANs, ACLs), and maintaining accurate user-to-role assignments in the identity store.
The authorization techniques employed by NAC—dynamic VLAN assignment, dynamic ACLs, and RBAC integration—represent a spectrum of control granularity. VLANs offer foundational, coarse-grained segmentation, creating separate logical networks. Dynamic ACLs provide a finer level of control, filtering specific traffic flows based on IP addresses and ports, often applied within or between VLANs. RBAC serves as the overarching policy framework, leveraging organizational roles to determine which VLANs and ACLs should be assigned to a user or device upon successful authentication. A mature NAC strategy typically combines these techniques synergistically. For example, RBAC determines a user belongs to the "Engineering" role, which dictates assignment to the "Engineering VLAN" (segmentation) and applies a specific dACL allowing access to development servers but blocking access to financial systems (fine-grained control), thereby achieving context-aware, least-privilege network access.
2.3. Endpoint Security Posture Assessment: Validating Device Health
Beyond verifying identity, NAC solutions often assess the security posture or "health" of endpoint devices before granting network access. This critical step helps prevent compromised, vulnerable, or non-compliant devices from connecting and potentially spreading malware or exposing sensitive data.
2.3.1. The Need for Health Checks
Endpoints represent a significant attack vector. Devices may lack essential security software, run outdated operating systems with known vulnerabilities, or be actively infected with malware. Allowing such devices onto the corporate network poses a substantial risk. Posture assessment acts as a health screening, ensuring devices meet a minimum security baseline before interacting with network resources.
2.3.2. Key Posture Assessment Checks
NAC solutions can perform a variety of checks, often configurable based on organizational policy. Common checks include:
Operating System (OS) Validation: Verifying the OS type and version (e.g., Windows 10, macOS Monterey) and checking if the latest security patches and service packs are installed. Timely patching is crucial for mitigating known vulnerabilities.
Antivirus/Anti-malware Software: Ensuring approved AV software is installed, running, and has up-to-date definition/signature files.
Host-Based Firewall Status: Checking if the personal firewall (e.g., Windows Defender Firewall, macOS Firewall) is enabled and configured according to policy.
Disk Encryption: Verifying that the device's hard drive is encrypted (e.g., using BitLocker or FileVault).
Presence of Required Software: Checking for mandatory applications, such as Endpoint Detection and Response (EDR) agents (e.g., CrowdStrike) or specific management tools (e.g., SCCM).
Absence of Prohibited Software: Scanning for unauthorized or blacklisted applications.
Configuration Compliance: Validating specific system settings against a defined security baseline.
2.3.3. Assessment Methods
NAC systems use different methods to gather posture information:
Agent-Based Assessment:
Persistent Agents: Software permanently installed on the endpoint that continuously monitors posture or performs checks periodically or upon network connection. These offer the most comprehensive visibility.
Dissolvable Agents: Temporary agents downloaded and executed during the network connection process (often initiated via web browser or login script). They perform checks, report results to the NAC server, and then remove themselves from the endpoint. They require no pre-installation but may have limitations and require user permissions to run.
Agentless Assessment: The NAC system attempts to gather posture information remotely using network protocols (e.g., WMI, SSH, SNMP) or by integrating with existing management systems like Active Directory, MDM (Mobile Device Management), or vulnerability scanners. Agentless methods are less intrusive but may provide less detailed information compared to agents, especially for non-domain-joined or personally owned devices.
2.3.4. Remediation and Quarantine
If a device fails the posture assessment, the NAC system enforces policy-defined actions:
Denial of Access: Blocking the device completely from the network.
Quarantine: Placing the device into a restricted network segment (quarantine VLAN) with limited connectivity. Access might be restricted to specific remediation resources, such as update servers (Windows Update, AV vendor sites), helpdesk portals, or websites providing instructions on how to fix the compliance issues.
User Notification: Informing the user about the compliance failure and guiding them through the remediation process.
Once the user addresses the issues (e.g., updates AV, installs patches), they can typically re-initiate the connection attempt, triggering another posture assessment. If the device now passes, it is granted appropriate network access.
While posture assessment is a powerful tool for ensuring endpoint hygiene, it faces challenges in today's diverse network environments. Standard checks for OS patches, AV status, and firewall configurations are primarily effective on traditional managed endpoints like Windows and macOS laptops. The proliferation of BYOD mobile devices and, particularly, IoT devices complicates posture assessment significantly. Many IoT devices run specialized operating systems, lack support for security agents, and cannot be easily patched or managed using traditional tools. Attempting universal, deep posture checks across such heterogeneous environments becomes impractical or impossible. This reality necessitates a more flexible and adaptive approach. While rigorous posture assessments remain crucial for managed corporate assets, alternative strategies are required for less manageable devices. These often involve leveraging NAC's device profiling capabilities to identify the device type and expected behavior, combined with stricter network segmentation (using MAB with dedicated VLANs and ACLs) and potentially behavioral analysis to detect deviations from normal activity. This highlights that effective NAC requires tailoring security controls to the capabilities and risks associated with different classes of endpoints, acknowledging that a one-size-fits-all posture check is often unrealistic.
3. NAC Enforcement Models: Pre-admission vs. Post-admission
NAC solutions enforce security policies using two primary models: pre-admission control and post-admission control. Many modern implementations utilize a hybrid approach combining elements of both.
3.1. Pre-admission Control
Pre-admission NAC operates on the principle of checking devices before they are granted access to the main network. It is the most common enforcement model. When a device attempts to connect (wired or wireless), the NAC system intercepts the connection and requires the device and/or user to successfully pass authentication and security posture checks based on predefined policies.
The typical workflow involves:
Device connects to a network port or SSID.
The network device (switch/AP), acting as a NAC enforcement point, blocks general traffic but allows communication with the NAC system/RADIUS server.
The NAC system performs authentication (e.g., 802.1X, MAB) and posture assessment (health checks).
If authentication and posture checks succeed, the NAC system authorizes access, potentially assigning a specific VLAN or ACL, and the network device permits traffic flow.
If checks fail, access is denied, or the device is placed in a quarantine/remediation network segment.
The primary advantage of pre-admission control is its proactive security stance. It prevents unauthorized or non-compliant devices from ever gaining access to potentially sensitive internal resources, significantly reducing the risk of infection or compromise originating from unhealthy endpoints. However, challenges can arise if policies are overly restrictive or if the NAC system experiences issues, potentially blocking legitimate users and impacting productivity. Careful planning, policy tuning, and phased implementation are crucial to mitigate user disruption.
3.2. Post-admission Control
Post-admission NAC focuses on monitoring and controlling devices after they have been granted initial network access. While some basic authentication might occur initially, the emphasis shifts to ongoing monitoring of device behavior and state.
The workflow typically involves:
Device connects to the network, possibly after passing minimal authentication checks.
The NAC system (or integrated monitoring tools) observes the device's network activity and potentially performs periodic re-assessments of its security posture.
If the NAC system detects a policy violation (e.g., device falls out of compliance, exhibits suspicious traffic patterns indicative of malware), it triggers an enforcement action.
Enforcement actions can include sending alerts to administrators, automatically re-assigning the device to a more restricted VLAN or applying a stricter ACL, or disconnecting the device from the network entirely.
The main advantage of post-admission control is a potentially smoother initial connection experience for users, as rigorous checks are deferred. It also allows the system to react to changes in device status or behavior that occur after the initial connection, such as a device becoming infected or a new critical vulnerability being discovered. However, the inherent drawback is that a malicious or non-compliant device might have a window of opportunity to cause harm before it is detected and contained. This model relies heavily on the speed and accuracy of the monitoring and response capabilities.
3.3. Hybrid Approaches
In practice, many contemporary NAC solutions implement a hybrid model that combines the strengths of both pre-admission and post-admission controls. This approach typically involves:
Strong Pre-admission Checks: Requiring robust authentication (ideally 802.1X) and essential posture validation before granting initial access.
Continuous Post-admission Monitoring: Ongoing surveillance of network behavior and periodic re-assessment of device compliance status.
Dynamic Response: The ability to automatically adjust a device's access privileges (e.g., change VLAN/ACL, quarantine) in real-time based on detected changes in posture or behavior.
This hybrid strategy aims to provide strong initial protection while maintaining the flexibility to adapt to evolving conditions and threats throughout a device's network session.
The selection of an enforcement model, or the balance within a hybrid model, often reflects an organization's specific security priorities, risk tolerance, and operational environment. Organizations handling highly sensitive data or operating under strict regulatory regimes may prioritize stringent pre-admission controls to minimize initial risk, even if it requires more careful tuning to avoid user friction. Conversely, environments with a high volume of unmanaged devices (like extensive guest networks or public Wi-Fi) might lean more heavily on initial ease of access followed by robust post-admission monitoring and segmentation, accepting a slightly higher initial risk in favor of user experience. The increasing emphasis on continuous verification in frameworks like Zero Trust suggests that hybrid models, performing checks both before and continually after admission, represent the most comprehensive approach, striving for security without unduly hindering legitimate access.
4. NAC Integration within the Security Ecosystem
Network Access Control solutions deliver maximum value when integrated into an organization's broader security architecture. Operating in isolation, NAC provides essential gatekeeping functions, but integration allows for context sharing and coordinated responses, transforming NAC into a dynamic enforcement point within a cohesive security strategy.
4.1. The Need for Integration
Modern cyber threats are often multi-faceted, and security requires a layered defense. No single tool has complete visibility or capability. Integrating NAC with other security systems enables:
Enhanced Context: NAC gathers rich information about users, devices, location, and posture. Sharing this context makes other tools (like firewalls) more intelligent and effective.
Improved Threat Detection: Correlating NAC events (e.g., authentication failures, posture non-compliance) with alerts from other systems (e.g., IDPS, EDR) can reveal sophisticated attacks that might otherwise be missed.
Automated Response: Integration facilitates automated actions across different platforms. For example, a threat detected by an EDR agent can automatically trigger a NAC quarantine action.
Streamlined Operations: Centralized logging and reporting (via SIEM) provide a unified view of security events, simplifying analysis and compliance reporting.
4.2. Integration Points
NAC solutions commonly integrate with various security technologies:
Firewalls (Especially Next-Generation Firewalls - NGFW): NAC can provide real-time user identity and device context (e.g., username, role, device type, OS, compliance status) to NGFWs. This allows firewalls to enforce policies based on user identity or group membership, rather than relying solely on static IP addresses, which is crucial in dynamic environments (DHCP, BYOD). Furthermore, NAC can dynamically instruct firewalls to alter access for specific users or devices based on changes in their authentication or compliance status (e.g., blocking internet access for a quarantined device).
Intrusion Detection/Prevention Systems (IDPS): An IDPS monitors network traffic for malicious activity or policy violations. When an IDPS detects a threat originating from or targeting a specific endpoint connected to the network, it can alert the NAC system. Based on this alert, NAC can automatically take enforcement action against the offending endpoint, such as moving it to a quarantine VLAN or blocking its network access completely, thus containing the threat rapidly.
Security Information and Event Management (SIEM) Systems: NAC systems generate valuable log data regarding authentication attempts (successes and failures), posture assessment results, policy enforcement actions, device profiling information, and administrative changes. Forwarding these logs to a SIEM platform enables centralized aggregation, correlation with events from other security sources (firewalls, servers, applications), long-term storage for forensics, advanced threat detection through analytics, and compliance reporting. SIEM dashboards can provide a holistic view of network access security.
Endpoint Detection and Response (EDR) / Antivirus (AV) Solutions: This integration is often bi-directional.
NAC checks EDR/AV: During posture assessment, NAC verifies that the required EDR or AV agent is installed, running, and up-to-date on the endpoint before granting access.
EDR/AV informs NAC: If the EDR/AV solution detects active malware, a policy violation, or a compromised state on an endpoint after it has connected, it can signal the NAC system. NAC can then automatically trigger an enforcement action, such as isolating the compromised endpoint in a quarantine VLAN to prevent the threat from spreading. Extended Detection and Response (XDR) platforms further enhance this by correlating data from endpoints, networks, cloud, and other sources, providing richer context for NAC enforcement decisions.
Vulnerability Management Systems: Integrating NAC with vulnerability scanners allows NAC policies to incorporate vulnerability data. For instance, NAC could automatically restrict network access for devices identified with critical, unpatched vulnerabilities until they are remediated.
Mobile Device Management (MDM) / Unified Endpoint Management (UEM) Systems: Integration provides NAC with richer context about managed devices, including ownership (corporate vs. personal), compliance status within the MDM/UEM framework, and installed applications. NAC can leverage this information for more granular policy decisions, and in some cases, trigger remediation actions via the MDM/UEM platform (e.g., forcing a policy update or application installation).
The bi-directional flow of information and enforcement actions enabled by these integrations is transformative. NAC systems collect detailed context about network connections—who the user is, what device they are using, its compliance status, and assigned access level. Sharing this context enriches the decision-making capabilities of other security tools, such as enabling identity-aware firewall rules or prioritizing alerts in the SIEM based on the user's role or device criticality. Conversely, NAC acts as a powerful enforcement point, capable of taking immediate action (quarantine, block, restrict access) based on triggers or intelligence received from other systems like IDPS or EDR. This elevates NAC from being merely a network gatekeeper to functioning as a central, context-aware policy enforcement engine within the security architecture. This capability is fundamental to achieving the goals of security orchestration, automation, and response (SOAR), enabling faster, more consistent, and automated responses to security events across the environment.
5. Comparative Analysis of Leading NAC Solutions
Selecting the right NAC solution requires careful evaluation of various factors, including features, scalability, integration capabilities, and alignment with existing infrastructure. The market features several prominent vendors, each with distinct strengths and approaches.
5.1. Introduction to Key Vendors
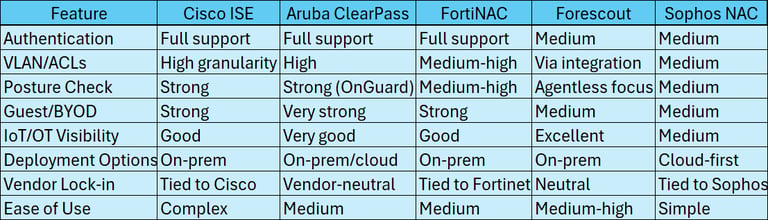
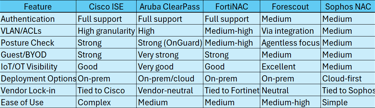
The user query specifically requested a comparison of Cisco ISE, Aruba ClearPass, FortiNAC, Forescout, and Sophos NAC. While other solutions exist (e.g., Portnox, Juniper Access Assurance, OPSWAT MetaDefender NAC, Armis), this analysis focuses on the requested five, drawing upon snippet details and general industry knowledge.
5.2. Comparison Criteria
To provide a structured comparison, the following criteria are considered:
Core Features: Support for key authentication methods (802.1X, MAB, Captive Portal), authorization capabilities (Dynamic VLAN/ACLs, RBAC), depth and methods of posture assessment, guest management features, BYOD onboarding and management, and visibility/control over IoT/OT devices.
Integration Capabilities: Breadth and depth of integration with third-party network infrastructure, security tools (Firewalls, SIEM, EDR, etc.), and identity management systems. Availability of APIs.
Deployment Models: Options available, such as physical appliances, virtual appliances, or cloud-based services (NACaaS).
Scalability: Suitability for different organization sizes, from small businesses to large, distributed enterprises.
Management Interface & Complexity: Ease of configuration, administration, and policy management. Perceived learning curve.
Strengths & Weaknesses: Key differentiators, common advantages, and potential drawbacks based on industry perception and available data.
Licensing Model: General approach to licensing (e.g., per endpoint, per user, feature-based tiers).
5.3. Vendor Profiles
Cisco Identity Services Engine (ISE):
Overview: A comprehensive policy control platform deeply integrated with Cisco's networking portfolio (switches, wireless controllers, firewalls, DNA Center).
Features: Robust support for 802.1X, MAB, various web authentication methods (LWA/CWA for guest/BYOD), dynamic VLAN/ACL assignment, posture assessment (agent-based), extensive profiling, guest lifecycle management, and integration with Cisco TrustSec for Security Group Tag (SGT)-based segmentation.
Integration: Strongest within the Cisco ecosystem but also integrates with many third-party vendors via RADIUS and APIs. Can work alongside other NACs like ClearPass for specific functions.
Deployment: Primarily hardware or virtual appliances.
Scalability: Highly scalable for large enterprise deployments.
Management: Powerful and feature-rich interface, but often perceived as complex with a significant learning curve.
Strengths: Deep Cisco integration, extensive feature set, scalability, TrustSec support.
Weaknesses: Complexity, potentially higher cost, strongest value proposition often tied to Cisco infrastructure.
Aruba ClearPass (HPE):
Overview: A widely adopted, vendor-agnostic NAC solution known for its flexibility and broad multivendor support.
Features: Comprehensive capabilities including 802.1X, MAB, advanced guest management (ClearPass Guest), BYOD onboarding (Onboard), posture assessment (OnGuard), extensive device profiling, and context sharing. Supports Central NAC cloud offering.
Integration: Excellent multivendor network device support and extensive ecosystem partnerships (security tools, MDM, etc.) via RADIUS, TACACS+, APIs.
Deployment: Hardware or virtual appliances. Cloud-managed options available via Aruba Central.
Scalability: Scales from medium to very large enterprises.
Management: Flexible and powerful policy engine. Can have a moderate to high learning curve due to its extensive customization options. Specific workflows like onboarding and certificate handling require careful configuration.
Strengths: Strong vendor-agnosticism, flexibility, comprehensive feature set (especially guest/BYOD), robust integrations.
Weaknesses: Can be complex to configure optimally, licensing can become intricate with add-on modules.
FortiNAC:
Overview: Fortinet's NAC solution, designed for tight integration within the Fortinet Security Fabric.
Features: Focuses on network visibility, control, and automated threat response. Supports 802.1X, MAB, guest portals, device profiling, vulnerability scanning integration, and automated segmentation. Emphasizes agentless scanning capabilities.
Integration: Deep integration with FortiGate (firewall), FortiSwitch, FortiAP, and FortiAnalyzer. Also supports integration with third-party network and security products.
Deployment: Hardware or virtual appliances.
Scalability: Suitable for various organization sizes, particularly those invested in the Fortinet ecosystem.
Management: Managed via its own interface, often integrated with Fortinet's management ecosystem (FortiManager). Configuration examples show specific FortiSwitch interactions.
Strengths: Seamless integration with Fortinet Security Fabric, strong automation capabilities, good visibility features.
Weaknesses: Strongest value proposition is within a Fortinet environment; may be less flexible in highly heterogeneous networks compared to vendor-agnostic solutions.
Forescout Platform:
Overview: A leader in agentless device visibility and control, particularly strong in IoT, OT (Operational Technology), and IoMT (Internet of Medical Things) environments. Mentioned as an alternative vendor.
Features: Excels at discovering, classifying, and assessing virtually any IP-connected device without requiring agents. Provides policy enforcement through dynamic network segmentation and integrations with network infrastructure (switches, routers, firewalls, wireless controllers) and other security tools.
Integration: Extensive library of integrations with a wide range of IT, IoT, OT, and security vendors.
Deployment: Typically deployed as hardware or virtual appliances.
Scalability: Designed for large, complex enterprise environments, including those with significant OT/IoT deployments.
Management: Comprehensive platform providing rich visibility dashboards and policy management capabilities.
Strengths: Unparalleled agentless visibility across diverse device types (IT, IoT, OT, IoMT), strong classification and assessment, extensive integrations.
Weaknesses: Primarily focused on visibility and control via integration; core authentication/RADIUS server functions might be less emphasized than in ISE/ClearPass. Can be a premium-priced solution.
Sophos NAC:
Overview: Sophos offers NAC capabilities, often integrated within its broader security ecosystem (Sophos Central). Mentioned as an AV/Security provider.
Features: Likely leverages Sophos Firewall, Sophos Switch, Sophos Wireless, and Sophos Intercept X (endpoint) for NAC functions. Utilizes Sophos Synchronized Security for context sharing between endpoint and network components. Core NAC features (authentication, guest access, basic posture) are expected.
Integration: Strongest integration within the Sophos product portfolio (Sophos Central). Third-party integration capabilities may be less extensive than specialized NAC vendors.
Deployment: Likely managed via Sophos Central (cloud) with enforcement via Sophos network hardware or endpoint agents.
Scalability: Typically targeted towards SMB and mid-market, though scalable.
Management: Managed through the unified Sophos Central console, potentially offering simpler administration for existing Sophos customers.
Strengths: Tight integration with Sophos ecosystem, potentially simpler management for Sophos shops, leverages Synchronized Security context.
Weaknesses: Likely less feature-rich or vendor-agnostic compared to leaders like ISE, ClearPass, or Forescout. Value proposition strongest for organizations already committed to the Sophos platform.
5.4. Comparative Table
The selection of a NAC solution is rarely based on features alone. The existing network and security infrastructure often plays a decisive role. Organizations heavily invested in Cisco networking may find ISE offers the most seamless integration and advanced features like TrustSec. Similarly, Fortinet customers benefit significantly from FortiNAC's integration within the Security Fabric. Conversely, organizations with highly heterogeneous, multivendor networks might prioritize the vendor-agnostic approach of Aruba ClearPass or Forescout. Furthermore, the primary driver for NAC adoption influences the choice. If the main goal is gaining deep visibility into unmanaged IoT/OT devices, Forescout's agentless capabilities are a major draw. If sophisticated guest and BYOD management is paramount, ClearPass often stands out. Ultimately, the "best" NAC solution depends heavily on the specific technical requirements, existing infrastructure, operational capabilities, and strategic security goals of the organization.
6. Implementation and Management: Challenges & Best Practices
Deploying and managing a Network Access Control solution is a significant undertaking that involves technical complexity, potential user impact, and ongoing maintenance. Understanding common challenges and adhering to best practices is crucial for a successful NAC implementation.
6.1. Common Implementation Challenges
Organizations often encounter several hurdles when deploying NAC:
Complexity: NAC systems interact with multiple network components (switches, controllers, RADIUS servers, identity stores, endpoints) and security policies. Designing, configuring, and troubleshooting these interactions requires significant expertise across networking, security, and identity management domains. Incorrect configuration can lead to widespread access issues.
Impact on Users: If not carefully planned and executed, NAC implementation can disrupt user workflow. Overly strict posture policies, inaccurate profiling, or cumbersome authentication processes can block legitimate access, leading to user frustration, increased helpdesk calls, and loss of productivity. Managing exceptions and troubleshooting individual connection problems can be resource-intensive.
Device Diversity (BYOD, IoT): Modern networks host a vast array of devices beyond traditional corporate laptops. Handling BYOD smartphones and tablets, along with numerous IoT/OT devices (printers, cameras, sensors, medical equipment, industrial controls), presents a major challenge. Many of these devices lack 802.1X supplicants, cannot run posture agents, and have limited management capabilities. Relying on insecure methods like MAB for these devices requires careful risk management. Accurately profiling and applying appropriate policies to this diverse ecosystem is difficult.
Legacy Systems: Older network infrastructure might lack necessary features like full 802.1X support or dynamic VLAN/ACL capabilities. Similarly, legacy operating systems or applications on endpoints may not be compatible with NAC agents or posture checks. Integrating NAC into environments with significant legacy components can require workarounds or infrastructure upgrades.
Policy Maintenance: NAC is not a static system. Security policies, user roles, device profiles, posture requirements (e.g., new OS patches, AV updates), and compliance mandates evolve. Keeping the NAC configuration aligned with these changes requires continuous monitoring, tuning, and administrative effort.
6.2. Best Practices for Deployment and Management
To navigate these challenges and maximize the benefits of NAC, organizations should follow established best practices:
Thorough Planning & Discovery: Before deploying NAC, invest significant time in understanding the existing environment. This includes mapping network topology, identifying all connected device types (corporate, BYOD, IoT, guest), understanding user roles and access requirements, analyzing current traffic flows, and clearly defining the business and security objectives for the NAC project. Gathering comprehensive data upfront is critical for effective policy design.
Define Clear and Realistic Policies: Develop well-defined, documented policies covering authentication methods, authorization rules (VLANs, ACLs), posture requirements, guest access procedures, BYOD guidelines, and IoT device handling. Start with foundational policies and iterate towards more granularity. Ensure roles used for RBAC are clearly defined and map appropriately to access needs. Avoid overly complex or stringent policies initially.
Phased Rollout and Monitoring Mode: Do not attempt a "big bang" deployment. Implement NAC in carefully planned phases, starting with less critical network segments or user groups. Critically, leverage the "monitor" or "audit" mode offered by most NAC solutions. In this mode, the NAC system logs policy decisions and potential violations without actually enforcing them (blocking access or quarantining). This allows administrators to observe the real-world impact of policies, identify misconfigurations or unexpected device behavior, and refine rules before switching to active enforcement, minimizing user disruption.
Robust Identity Management: NAC relies heavily on accurate identity information. Ensure backend identity directories (e.g., Active Directory, Azure AD, Okta) are well-maintained, with up-to-date user accounts, group memberships, and timely de-provisioning of departing employees. Inaccurate identity data leads to incorrect authorization.
Leverage Device Profiling: Actively use the NAC system's profiling capabilities to automatically discover, identify, and classify devices connected to the network, especially those that cannot authenticate via 802.1X (like IoT). Use this profile information (e.g., device type, OS, manufacturer) to apply appropriate baseline security policies, such as assigning them to segmented VLANs, even if full authentication or posture assessment isn't possible.
Secure MAB Implementations: When MAB is unavoidable for legacy or IoT devices, treat it as a high-risk exception. Combine MAB with device profiling to detect spoofing attempts. Enforce strict network segmentation using dedicated VLANs and highly restrictive ACLs that permit only essential communication for MAB devices. Monitor MAB authentications and device behavior closely. Consider Layer 2 encryption like MACsec where feasible to protect against sniffing and spoofing on wired segments.
Continuous Monitoring, Auditing, and Tuning: NAC requires ongoing attention. Regularly review NAC logs and reports to identify trends, anomalies, and policy effectiveness. Audit policies and role assignments periodically. Update posture requirements promptly as new patches and AV signatures are released. Adapt policies based on changes in the threat landscape, network infrastructure, or business needs.
Automation and Integration: Leverage NAC's integration capabilities to automate responses. Configure NAC to automatically quarantine devices based on alerts from SIEM, EDR, or IDPS systems, reducing manual intervention and response times.
Successful NAC implementation hinges not just on selecting the right technology but equally on meticulous planning, robust processes, and effective communication. The challenges encountered often stem from underestimating the complexity, failing to adequately prepare the environment (especially identity management), or neglecting the impact on end-users. Best practices emphasize a data-driven approach (discovery, monitoring mode), clear policy definition tied to business needs, a gradual rollout to manage risk and user impact, and recognizing that NAC is a continuous process requiring ongoing maintenance and adaptation. Treating NAC deployment as a strategic security project involving collaboration between networking, security, identity management teams, and potentially business stakeholders, rather than just a technology rollout, is paramount for achieving the desired security outcomes without crippling operations.
7. NAC Application Across Industries (Detailed Examples)
Network Access Control provides foundational security capabilities applicable across various industries. However, the specific implementation details, policy priorities, and focus areas often differ based on industry-specific risks, regulatory requirements, user populations, and device types.
7.1. Corporate Networks
In typical corporate environments, NAC addresses the need to differentiate access for employees, guests, and increasingly, BYOD devices, while protecting corporate assets and intellectual property.
Employee Access: The primary goal is secure and role-appropriate access. Employees typically authenticate using 802.1X, often with corporate credentials integrated with Active Directory or via digital certificates deployed to managed devices. Posture assessment ensures corporate laptops meet security standards (e.g., up-to-date OS patches, active endpoint security software, disk encryption). RBAC is heavily utilized, with dynamic VLAN assignment and/or ACLs placing employees into network segments corresponding to their department or role (e.g., Finance, Engineering, HR), enforcing least-privilege access to relevant resources.
Guest Access: Providing internet access for visitors without compromising internal security is key. A captive portal is the standard mechanism, offering self-registration, sponsored access (where an employee approves the guest), or voucher-based login. Guests are always placed in a highly segmented VLAN, typically with access only to the internet and strictly isolated from all internal corporate resources. Access is usually time-limited.
BYOD Management: Supporting employee-owned devices requires balancing usability with security. Onboarding often occurs via a captive portal that may facilitate registration and potentially deploy configuration profiles or agents. Posture checks might be performed, possibly with slightly relaxed requirements compared to corporate devices, or focusing on essentials like OS version and screen lock. RBAC still applies, granting access based on the employee's role, but potentially with more restrictive ACLs than if they were using a corporate device. BYOD devices are typically segmented into a dedicated VLAN, separate from both guest and corporate networks.
7.2. Healthcare (HIPAA Compliance Focus)
Healthcare environments present unique challenges due to the critical need to protect sensitive electronic Protected Health Information (ePHI) under regulations like HIPAA, and the proliferation of specialized Internet of Medical Things (IoMT) devices.
Protecting Patient Data (ePHI): NAC enforces strict access controls to systems containing ePHI. Clinical staff authenticate using strong methods (often 802.1X). RBAC is critical, ensuring that roles (e.g., doctor, nurse, technician, billing staff) grant access only to the specific patient data and applications necessary for their job function. Dynamic VLANs and ACLs segment networks to isolate clinical workstations and EMR systems. Audit logs generated by NAC are essential for demonstrating HIPAA compliance.
Securing Medical Devices (IoMT): A major challenge involves securing numerous IoMT devices (infusion pumps, patient monitors, imaging equipment) that often run legacy OS, cannot support 802.1X or agents, and may have known vulnerabilities. NAC strategies rely heavily on:
Profiling: Identifying devices based on MAC address, DHCP fingerprint, protocol usage, etc.
MAB: Using MAC addresses for basic authentication, acknowledging the inherent risks.
Micro segmentation: Placing identified IoMT devices into highly restricted VLANs, often one VLAN per device type or function. Strict ACLs are applied, permitting communication only with explicitly authorized destinations (e.g., specific management servers, data gateways) and blocking all other traffic.
Continuous Monitoring: Closely monitoring IoMT device traffic for anomalies or policy violations.
Guest Wi-Fi: Providing internet access for patients and visitors is common, but must be rigorously isolated. A separate guest network using a captive portal is deployed, with no connectivity path to the clinical network or systems handling ePHI.
7.3. Education (Managing Diverse Users & Devices)
Educational institutions, from K-12 to higher education, face challenges of scale, extreme device diversity (student BYOD), and the need to support various user roles (students, faculty, staff, researchers, guests) across large campuses.
Student Device Management: With BYOD being the norm, NAC must handle a massive influx of student-owned laptops, tablets, and smartphones. Captive portals are frequently used for initial onboarding, requiring login with university credentials and acceptance of Acceptable Use Policies (AUPs). Dynamic VLAN assignment segments the network, often separating residential hall networks (dormitories) from academic networks. Policies may include bandwidth shaping or content filtering based on user role or network location.
Faculty/Staff Access: Faculty and staff typically require more privileged access to administrative systems, research databases, and teaching resources. 802.1X authentication is preferred for university-managed or registered personal devices, often coupled with posture checks. RBAC differentiates access levels between faculty, administrative staff, IT personnel, etc.
Lab and Classroom Computers: Shared computers in labs or classrooms can be secured using 802.1X machine authentication (using device certificates) or potentially MAB depending on the management capabilities. NAC ensures consistent policy enforcement regardless of whether connection is wired or wireless.
Guest/Visitor Access: Campuses often host events and visitors. A simple, often open or self-registration-based captive portal provides temporary, internet-only access, isolated from internal academic and administrative networks.
Observing these industry applications reveals how the core capabilities of NAC are prioritized differently based on context. Corporate environments focus heavily on differentiating employee, guest, and BYOD access using RBAC and standard posture checks. Healthcare places an extreme emphasis on segmentation and specialized handling of unmanageable IoMT devices, driven by compliance mandates like HIPAA and the sensitivity of patient data. Education must contend with massive scale, BYOD dominance, and the need to support a wide spectrum of user roles with varying access requirements, making scalable onboarding and robust segmentation critical. While the fundamental tools of NAC (authentication, authorization, posture, segmentation) remain the same, their application and the specific features emphasized (e.g., IoMT profiling in healthcare, scalable guest management in education) are tailored to address the unique risks, user populations, device ecosystems, and regulatory landscapes of each sector. This underscores the importance for organizations to evaluate NAC solutions not just on a generic feature list, but on their ability to effectively address industry-specific challenges.
8. NAC and Regulatory Compliance
Network Access Control plays a significant role in helping organizations achieve and maintain compliance with various industry regulations and security frameworks. By providing mechanisms for enforcing access policies, segmenting networks, ensuring endpoint health, and generating audit trails, NAC offers tangible proof of control implementation.
8.1. The Role of NAC in Compliance
Compliance mandates often require organizations to implement specific technical controls related to network access, data protection, and system integrity. NAC directly addresses many of these requirements by:
Enforcing Policy: Translating written security policies into automated, enforceable network access rules.
Limiting Access: Ensuring only authorized users and compliant devices can connect to sensitive parts of the network.
Providing Visibility: Offering insights into who and what is connected, which is crucial for audits and incident response.
Generating Audit Logs: Creating detailed records of access attempts, authentication outcomes, posture status, and enforcement actions, providing evidence for auditors.
8.2. Specific Framework Examples
PCI DSS (Payment Card Industry Data Security Standard): This standard mandates strict security controls for organizations handling credit card data. NAC contributes significantly to meeting several PCI DSS requirements:
Req 1: Install and maintain a firewall configuration to protect cardholder data: NAC enforces network segmentation (via VLANs/ACLs) to isolate the Cardholder Data Environment (CDE) from other network segments, limiting the scope of PCI DSS assessments.
Req 7: Restrict access to cardholder data by business need-to-know: NAC enforces role-based access, ensuring only authorized personnel can access network segments containing cardholder data.
Req 8: Identify and authenticate access to system components: NAC provides robust authentication mechanisms (802.1X) for users and devices accessing the network.
Req 10: Track and monitor all access to network resources and cardholder data: NAC generates detailed logs of access events, which can be fed into a SIEM for monitoring and auditing.
HIPAA (Health Insurance Portability and Accountability Act): HIPAA requires healthcare organizations to protect the confidentiality, integrity, and availability of electronic Protected Health Information (ePHI). NAC helps meet HIPAA Security Rule requirements:
Access Control (§ 164.312(a)): NAC implements technical policies and procedures to allow access only to authorized persons or software programs. It enforces unique user identification, authentication, and role-based access controls.
Audit Controls (§ 164.312(b)): NAC systems generate logs documenting access attempts and policy enforcement actions, supporting audit requirements.
Transmission Security (§ 164.312(e)): While primarily focused on data in transit, NAC contributes by ensuring only authorized and potentially posture-checked devices can connect to networks transmitting ePHI. Network segmentation enforced by NAC helps protect ePHI by isolating systems that process or store it.
NIST (National Institute of Standards and Technology) Frameworks: Frameworks like the NIST Cybersecurity Framework (CSF) and Special Publication 800-53 provide comprehensive security guidelines widely adopted by government agencies and private sector organizations. NAC aligns with numerous controls within these frameworks, particularly in the following families:
Access Control (AC): NAC directly implements controls related to account management, access enforcement (policy decision point/policy enforcement point), separation of duties (via RBAC), least privilege, and remote access control.
Identification and Authentication (IA): NAC enforces requirements for identifying and authenticating organizational users and devices.
System and Information Integrity (SI): NAC's posture assessment capabilities contribute to ensuring system integrity by checking for malware, patch status, and configuration compliance before allowing network access.
GDPR/Other Data Privacy Regulations: While broader in scope, data privacy regulations emphasize protecting personal data. NAC supports this by enforcing least-privilege access, ensuring only authorized users and systems can access networks containing personal data, thereby minimizing unauthorized exposure or processing.
8.3. Key NAC Contributions to Compliance
Across various frameworks, NAC consistently contributes by providing mechanisms for:
Policy Enforcement: Automating the application of access control rules.
Network Segmentation: Isolating sensitive systems and data flows (e.g., CDE, networks with ePHI, critical infrastructure segments).
Strong Authentication: Verifying identities before granting access.
Endpoint Compliance: Validating device security posture against defined baselines.
Auditing and Reporting: Generating verifiable evidence of control implementation and operation.
A significant benefit of implementing NAC for compliance purposes lies in its ability to provide demonstrable evidence of control effectiveness. Compliance frameworks and auditors require organizations not only to define security policies but also to prove that these policies are consistently enforced. NAC systems achieve this by actively implementing controls (authentication, authorization via VLANs/ACLs, posture checks) and generating detailed logs that serve as an audit trail. This automated enforcement and logging capability significantly streamlines the process of preparing for and undergoing audits, providing concrete proof that access control measures are functioning as intended. Therefore, investing in NAC can be a strategic move not only to improve security but also to simplify and strengthen an organization's compliance posture.
9. Advanced NAC Concepts and Future Trends
Network Access Control continues to evolve beyond traditional gatekeeping, adapting to new security paradigms, network architectures, and device types. Several advanced concepts and emerging trends are shaping the future of NAC.
9.1. NAC and Zero Trust Architecture (ZTA)
Zero Trust Architecture (ZTA) represents a fundamental shift in security thinking, moving away from perimeter-based trust towards a model of "never trust, always verify". ZTA assumes that no user or device should be implicitly trusted based on its network location (inside or outside the traditional perimeter). Instead, every access request must be explicitly verified based on identity, device health, context, and policy before granting granular, least-privilege access to specific resources.
NAC is not synonymous with Zero Trust, but it serves as a critical policy enforcement point and enabler within a ZTA framework. Key NAC capabilities directly support ZTA principles:
Identity Verification: NAC authenticates users and devices for every access attempt.
Device Posture Assessment: NAC continuously verifies device health and compliance against policy.
Least-Privilege Access: NAC enforces granular authorization (VLANs, ACLs, SGTs) based on real-time policy decisions, granting access only to necessary resources.
Dynamic Segmentation: NAC enables micro segmentation, isolating resources and limiting lateral movement based on verified identity and context.
Continuous Monitoring: Advanced NAC solutions monitor sessions post-admission, potentially revoking access if risk posture changes.
In a ZTA, NAC integrates with other components (like identity providers, threat intelligence feeds, endpoint security tools) to make dynamic, context-aware access decisions for each connection attempt, enforcing the principle of continuous verification.
9.2. Cloud-Based NAC (NACaaS)
Traditionally, NAC solutions were deployed as on-premises hardware or virtual appliances. However, there is a growing trend towards cloud-delivered NAC, often referred to as NAC-as-a-Service (NACaaS). Examples mentioned in the snippets include Portnox Cloud, Aruba Central NAC, and OPSWAT MetaDefender NAC Cloud.
Benefits of NACaaS include:
Simplified Deployment: Eliminates the need for on-premises server infrastructure, reducing deployment time and complexity. Cloud RADIUS services can often be provisioned quickly.
Scalability: Cloud platforms offer inherent scalability to accommodate growing numbers of users and devices.
Centralized Management: Provides a single console for managing policies across distributed locations.
Accessibility: Easier support for remote and mobile workforces connecting from various locations.
Automatic Updates: Cloud providers handle platform maintenance and feature updates.
Considerations for NACaaS include potential data privacy concerns (depending on where data is processed and stored), reliance on stable internet connectivity for policy enforcement and authentication, and ensuring seamless integration with any remaining on-premises resources or identity stores.
9.3. Enhancing IoT/OT Security
Securing the rapidly expanding Internet of Things (IoT) and Operational Technology (OT) landscape remains a significant challenge for NAC. These devices often lack standard security features and management capabilities. Advanced NAC approaches focus on:
Deep Agentless Profiling: Utilizing passive network analysis, AI/ML techniques, and integration with specialized databases to accurately identify and classify a wide range of IoT/OT devices without requiring agents.
Behavioral Analysis: Monitoring the typical network behavior of IoT/OT devices and detecting anomalies that could indicate compromise or malfunction.
Granular Micro segmentation: Employing dynamic ACLs, firewall integration, or Software-Defined Networking (SDN) / fabric technologies to create highly specific communication policies for each device or device type, strictly limiting their network access to only what is absolutely necessary (e.g., communication only with a specific cloud platform or management server).
Integration with Specialized Platforms: Partnering with dedicated IoT/OT security solutions (like Armis or Forescout) that provide deeper visibility and threat detection capabilities specific to these environments.
9.4. Increased Automation and Orchestration (SOAR Integration)
The trend towards Security Orchestration, Automation, and Response (SOAR) heavily involves NAC. SOAR platforms integrate various security tools to automate incident response workflows. In this context, NAC acts as a key automated enforcement point. For example, if a SIEM or EDR system detects a critical threat associated with an endpoint, a SOAR playbook can automatically trigger the NAC system to immediately isolate or block that endpoint, containing the threat much faster than manual intervention would allow.
9.5. Convergence with SASE/SSE
As organizations adopt cloud services and support remote workforces, security architectures are evolving towards Secure Access Service Edge (SASE) and its subset, Security Service Edge (SSE). These frameworks converge networking and security functions (like SWG, CASB, ZTNA, FWaaS) into cloud-delivered services. NAC principles – verifying user identity, assessing device posture, and enforcing context-aware policy – are fundamental to ZTNA components within SASE/SSE. While traditional NAC focuses primarily on LAN/WLAN access, its core concepts are merging with these broader frameworks to provide consistent policy enforcement for users accessing resources from anywhere, whether on-premises or in the cloud.
The evolution highlighted by these trends—integration with Zero Trust, the rise of cloud delivery, enhanced IoT/OT strategies, and deeper automation—indicates that NAC is transforming. It is moving beyond its origins as a static network gatekeeper for the corporate LAN towards becoming a dynamic, intelligent, and highly integrated policy enforcement engine. Its role is expanding to manage access across hybrid environments (on-premises, cloud, remote) based on a continuous assessment of risk derived from richer context (identity, device state, behavior, location, threat intelligence). The future of NAC lies in its adaptability and its ability to serve as a central enforcement mechanism within comprehensive, context-aware security architectures like ZTA and SASE, ensuring secure access for any user, from any device, to any resource, anywhere.
10. Conclusion: The Strategic Importance of NAC
Network Access Control has firmly established itself as an indispensable component of modern cybersecurity strategy. This analysis has detailed its core functions, operational mechanisms, and critical role in addressing the security challenges posed by today's complex and distributed network environments.
The core mechanisms of NAC—robust authentication (via 802.1X, MAB, captive portals), granular authorization (through dynamic VLANs, ACLs, and RBAC integration), and essential endpoint security posture assessment—provide the foundation for enforcing security policies at the network edge. The choice between pre-admission and post-admission enforcement models, or more commonly a hybrid approach, allows organizations to balance proactive security with operational needs.
Crucially, NAC's value is significantly amplified through integration with the broader security ecosystem, including firewalls, IDPS, SIEM, and EDR solutions. This integration transforms NAC from an isolated gatekeeper into a contextual security hub capable of sharing intelligence and acting as an automated enforcement point, enabling faster and more effective responses to threats. While the vendor landscape offers diverse solutions, selection often depends on specific organizational needs, existing infrastructure, and strategic priorities like IoT visibility or BYOD management.
Despite its power, implementing and managing NAC presents challenges related to complexity, user impact, and device diversity. Adherence to best practices—thorough planning, phased rollouts using monitor mode, clear policy definition, robust identity management, and continuous monitoring—is essential for success. NAC's applicability across various industries, from corporate networks to healthcare and education, highlights its versatility, although specific priorities and configurations vary based on sectoral risks and regulations. Furthermore, NAC plays a vital role in achieving and demonstrating compliance with standards like PCI DSS, HIPAA, and NIST by providing tangible evidence of access control enforcement.
Looking ahead, NAC is evolving rapidly. Its alignment with Zero Trust Architecture, the shift towards cloud-based NACaaS offerings, enhanced capabilities for securing IoT/OT devices, and increased automation underscore its adaptability. NAC is no longer just about controlling initial access to the LAN; it is becoming a dynamic policy enforcement engine crucial for securing hybrid environments and enabling modern security paradigms.
In conclusion, Network Access Control provides essential visibility, granular control, and automated enforcement capabilities that are fundamental to securing contemporary networks. It directly addresses the risks associated with device proliferation, user mobility, and sophisticated threats while supporting compliance objectives. As networks continue to evolve and threats become more advanced, NAC's strategic importance as a foundational and adaptive security control will only continue to grow, making it a critical investment for any organization committed to protecting its digital assets.