A guide on Network Access Control (NAC)
Network Access Control (NAC) is a major piece of today’s cybersecurity strategy. It gives organizations a way to control who and what can connect to their networks. As networks grow with more personal devices, IoT, remote workers, and constant threats, perimeter security alone can’t cut it. NAC fills this gap by using policies to decide access, no matter where a user or device connects from.
1. What is NAC?
NAC checks who’s trying to connect to the network and what device they’re using. It then allows or denies access based on rules. It also keeps an eye on what happens after the connection is made.
2. Why Do We Need NAC?
Today’s networks are messy: personal and IoT devices, remote workers, cyber threats. NAC steps in by giving visibility and control based on identity, device, location, and security health.
3. What Does NAC Do?
Main Goals: Stop unauthorized access, help with compliance, show what’s connected, automate access controls, support BYOD and IoT securely.
4. How NAC Works
Includes authentication methods (802.1X, MAB, captive portals), authorization via VLANs/ACLs/RBAC, and device posture checks.
5. Enforcement Models
Pre-admission (check before access), post-admission (monitor after), or hybrid (do both).
6. Integration with Other Security Tools
NAC works best when it shares info with firewalls, IDPS, SIEM, EDR, and MDM tools.
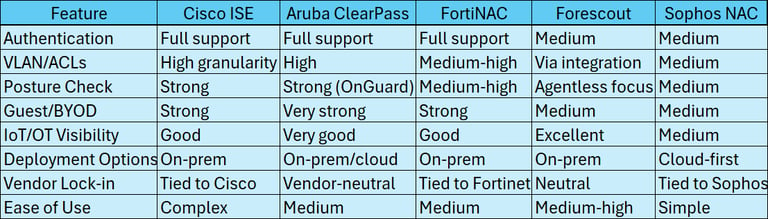
7. Vendor Comparison
Table of Cisco ISE, Aruba ClearPass, FortiNAC, Forescout, and Sophos NAC based on features like authentication, posture check, deployment.
8. Deployment Tips
Plan first, start in monitor mode, define roles, profile devices, limit MAB, keep watching, and automate actions.
9. Use Cases by Industry
Corporate: RBAC, BYOD. Healthcare: Secure medical devices and patient data. Education: Handle massive BYOD and guest users.
10. Compliance Support
NAC helps meet PCI DSS, HIPAA, NIST, and GDPR by enforcing and logging access policies.
11. Where NAC is Heading
Zero Trust, Cloud NAC, IoT/OT security, automation (SOAR), and integration with SASE.
Conclusion
NAC gives the visibility, control, and enforcement needed to keep networks secure as they grow and change.